How Does the Email System Work? A Beginner’s Guide to Digital Communication

Email — how does it really work?
Just consider how quickly a message can travel across the globe, connecting people in an instant. But what happens behind the scenes when you click “Send”? The process is far more complex than it seems, involving a series of technologies and steps that ensure your message reaches its destination safely and efficiently.
Each step is vital in getting your message from your device to the recipient’s inbox. By exploring the process from composing an email to its delivery, you can gain a deeper appreciation for the complexities of digital communication. It can also assist in identifying and resolving issues when complications arise.
This article will provide a detailed breakdown of the email delivery process, offering a comprehensive understanding of how your message is transmitted and received.
1. Composing the Email
When composing an email using an email application or website (commonly referred to as an email client, such as Gmail, Outlook, or Yahoo Mail), there are several key sections you need to fill out to ensure your message is complete and clear:
- Recipient: This is the email address of the person or people you’re sending the email to. Ensure the address is correct, as a single typo can result in the email not being delivered. You may also see options for:
- Cc (Carbon Copy): All recipients can see who else received the email.
- Bcc (Blind Carbon Copy): Recipients are hidden from one another, offering more privacy.
These options allow you to send the email to additional recipients.
- Subject: A concise and clear summary of the email’s purpose which helps the recipient quickly understand the email’s content and prioritize it.
- Body: The main content of your email, where you communicate your message.
- Attachments (Optional): Files or images you include in the email. Attachments can include documents, spreadsheets, or images that support the message you’re conveying.
Once everything is ready, click the Send button. Your email is then transmitted through the internet to the recipient’s email server, where it will appear in their inbox.
Once everything is ready, click the Send button. Your email is then transmitted through the internet to the recipient’s email server, where it will appear in their inbox.
2. Outgoing Mail Server
Once you click “Send,” your email client establishes a connection with an SMTP server (Simple Mail Transfer Protocol), which functions as the digital equivalent of a post office, overseeing the initial stages of email delivery. The first step the SMTP server takes is to verify the validity of your email, ensuring that it adheres to the required protocols and standards for transmission. Once the email passes this validation, the server then proceeds to determine the correct destination by analyzing the domain name in the recipient’s email address—the part following the “@” symbol. For instance, when you send an email to someone at “example.com,” the SMTP server finds the correct mail server for that domain
3. Recipient’s Mail Server
The SMTP server communicates with the DNS to locate the recipient’s mail server. The DNS acts like a directory for the internet, mapping domain names to IP addresses and identifying the Mail Exchange (MX) record for the recipient’s domain. The MX record specifies the mail server responsible for handling emails for that domain, ensuring that the message is directed to the correct server. This step is crucial for accurate email routing, as it helps the SMTP server identify the appropriate destination for the message based on the domain’s settings. Once the recipient’s server is located through the DNS, the SMTP server can then establish a connection and transfer the email, ensuring that it reaches the intended recipient without any errors or delays. This process plays an essential role in maintaining the efficiency and reliability of email delivery systems.
4. Transferring the Email
Once the SMTP server has the recipient’s server information, it transfers the email. Emails often pass through multiple servers on their journey across the internet, each playing a crucial role in directing the message toward its final destination. These servers perform various tasks, such as checking the validity of the recipient’s domain and routing the message based on the best available path. Along the way, the email may pass through security filters to detect spam or malicious content, ensuring the integrity of the message. These servers work together to guarantee that the email follows the most efficient and secure path to reach its destination, minimizing delays and ensuring reliable delivery.
5. Storing the Email
When the email arrives at the recipient’s mail server, it is stored until the recipient retrieves it. The email is typically stored in the recipient’s mailbox, where it remains until accessed. This process ensures that the message is safely kept until the recipient is ready to view it. There are two primary protocols used for accessing email:
- IMAP (Internet Message Access Protocol): allows emails to be stored on the server, providing users with the ability to access their messages from multiple devices. This ensures that emails remain synchronized across all devices, allowing users to read, reply, and manage their inboxes seamlessly. Unlike other protocols, IMAP enables users to leave emails on the server, ensuring that messages are consistently available, regardless of the device being used. This flexibility makes IMAP a preferred choice for individuals who need to access their email on various platforms, such as smartphones, tablets, and computers.
- POP3 (Post Office Protocol): an older email protocol that downloads emails to a single device and removes them from the server, typically leaving the messages stored locally on that device. While it was once the standard for accessing email, it is less commonly used in modern email systems. This is largely because IMAP offers greater flexibility by allowing users to synchronize emails across multiple devices, ensuring that messages are accessible from anywhere and remain consistent across platforms.
6. Delivering to the Inbox
Finally, the recipient’s email client connects to their mail server and downloads the email. They can now view and respond to the message, completing the communication process. Once the message is retrieved, the recipient can review its contents and take appropriate action. This seamless flow ensures efficient and reliable communication between sender and recipient.
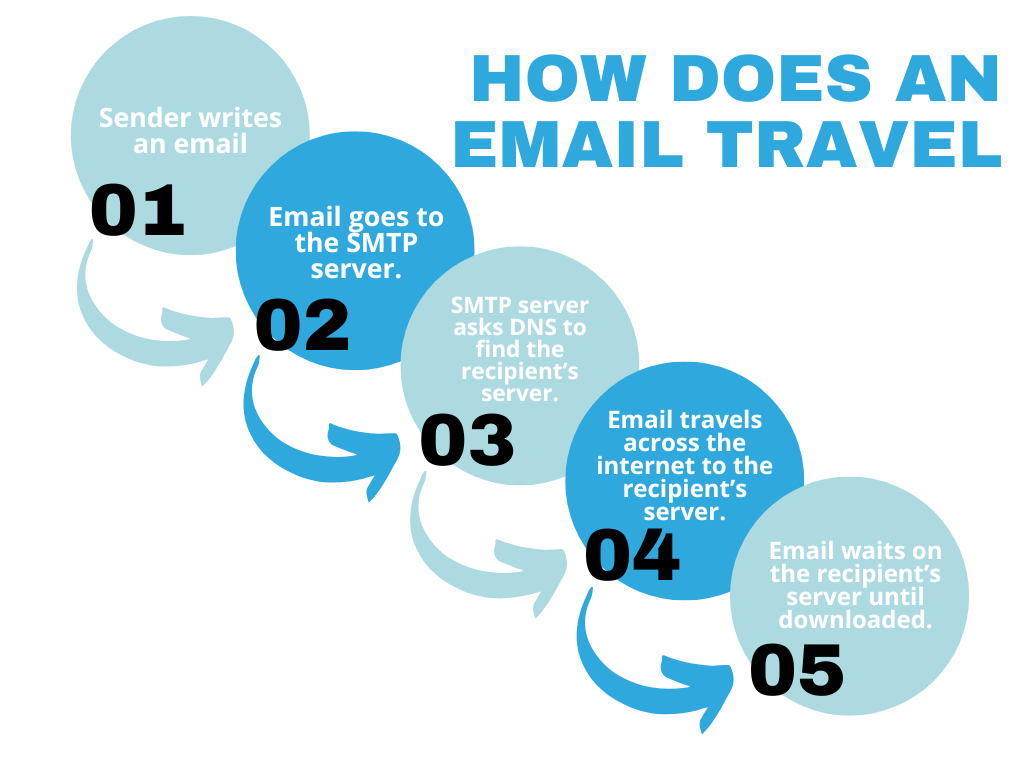
7. How Does an Email Travel?
When you send an email, it embarks on a journey across the internet to reach its destination. The process involves multiple systems working together to ensure your message is delivered accurately and securely. From the moment you hit “send,” the email travels through servers, networks, and protocols, navigating to the recipient’s inbox. The diagram below outlines the step-by-step path of how an email travels from the sender to the recipient, illustrating the journey behind every message you send:
8. Security Features
Modern email systems incorporate a range of sophisticated security measures to protect messages during transmission and ensure they are delivered to the intended recipient. These include:
- Encryption: A critical component of email security, designed to protect messages during transmission across networks. By encrypting an email’s contents, unauthorized individuals cannot read or access sensitive information, even if they intercept the data. Protocols like SSL (Secure Sockets Layer) and TLS (Transport Layer Security) ensure that the connection between email servers remains secure, creating a private communication channel. These protocols are especially vital when sending emails containing confidential information, as they prevent data breaches and maintain the integrity of the message throughout its journey.
- Authentication: Verifies the legitimacy of emails and ensures they originate from trusted sources. Tools such as SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) validate the sender’s domain and protect against email spoofing, a common tactic used in phishing attacks. SPF checks whether an email comes from an authorized server for the sender’s domain, while DKIM uses cryptographic signatures to verify the email’s authenticity. Together, these mechanisms bolster trust in email communication by reducing the risk of fraudulent messages and protecting recipients from potential cyber threats.
- Spam Filters: An email system defense mechanism, designed to detect and block unwanted or harmful messages. To identify potential risks, these filters analyze incoming emails based on various criteria, such as suspicious keywords, unusual sender behavior, or known malicious domains. By reducing the influx of spam, phishing attempts, and malware-laden emails, spam filters not only enhance user productivity but also significantly decrease the likelihood of falling victim to cyberattacks.
9. Why Understanding Email Matters
While sending and receiving emails might seem simple, the underlying processes are remarkably complex, relying on multiple technologies working seamlessly together. From servers and protocols to encryption and data storage, each step is carefully designed to ensure swift and reliable communication. Gaining insight into these processes highlights the sophistication of email systems and underscores the critical role of cybersecurity in safeguarding sensitive information. By understanding these mechanisms, users can better appreciate the importance of maintaining secure practices to protect their digital interactions.
Conclusion
Sending an email involves numerous steps and advanced technologies working harmoniously, yet the entire process is completed within seconds. Behind this seemingly effortless action is a network of protocols, servers, and encryption methods ensuring the message reaches its destination accurately and securely. The next time you send an email, you’ll be aware of the journey it takes through the digital landscape. By understanding how email systems operate, you can make informed decisions to enhance the security of your messages, safeguard sensitive information, and contribute to safer communication in an increasingly interconnected world.