How to Prevent Phishing Attacks: 22 Email Management Tips Your Organization Should Embrace Before It’s Too Late
Hackers who create phishing attacks are constantly changing techniques, developing different methods to trick unsuspecting users and convince them to believe their email messages are legit. The reasons these hackers are often successful in their deception is because they prey on a basic human trait: trust.
This is especially dangerous in business settings — where it’s not just your employees’ information that is at risk of being stolen, it’s your entire organization and its customers that are vulnerable.
There are a few ways you can protect yourself. By embracing some simple email management tips and creating your own internal set of email best management best practices at work, you will ensure your organization is buttoned up from any future phishing attacks.
The first step is to get to know the types of phishing attacks out there.
Types of Phishing Attacks
Most users are unaware as to how you can identify a phishing email, but the easiest step you can take to prevent phishing attacks is to simply increase their awareness of the threat.
Phishing is, by definition, any attempt to obtain sensitive information for malicious reasons, accomplished by posing as a trustworthy source in electronic communications. In its most basic form, it involves sending out a wide net of emails containing harmful links or traps for unsuspecting users.
These are some of the common variants of phishing:
- Spear Phishing: Attempts directed at specific individuals, companies, or political organizations. These attacks are often well-crafted, and in some cases, are tailored specifically to appear personal to the target.
- Smishing (SMS Phishing): Attacks using SMS (cell phone text messages) as bait to cause people to divulge sensitive personal information.
- Pharming: Cyber-attacks which redirect traffic from a legitimate website to another, fake site. This typically involves corruption in DNS server software or the targeting of a local network router.
- Covert Redirect: Similar to Pharming, a covert redirect makes links appear legitimate, when in actuality they lead to the attacker’s website. This is typically done using a corrupted login pop-up window.
- Clone Phishing: An attack using a seemingly legitimate communication which has been identically replicated using a previously delivered/received message.
- Whaling: The practice of attacking high-profile targets within businesses. These are often disguised as legal subpoenas, complaints from customers, or other “executive” issues.
- Link Manipulation: A common attack which disguises the malicious link as a link to a reputable or familiar webpage.
- Content-Injection Phishing: A technique where the attacker changes part or all of the content found within the page of a reliable website, which is used to direct the user to another site designed to obtain their personal information.
- Filter Evasion: An attempt to avoid anti-phishing filters by using images containing writing, as opposed to actual text.
- Website Forgery: Attacks which manipulate a malicious website’s appearance so that it appears to have a legitimate URL.
- Man-in-the-Middle Phishing: A sophisticated phishing technique where an attacker collects personal information by hiding in between the original website and a phishing system and tracing the details as they are entered.
- Search Engine Phishing: An attack which directs users to falsified product websites and collects personal information as the user inputs their data.
- Tabnabbing/Tabjacking: An attack which takes advantage of a browser with multiple open tabs, and silently loads and redirects the user to a fraudulent site.
Now that you have the most common types of phishing attacks, the next step is understanding how to identify them when they occur.
Top Signs You’re Under a Phishing Attack
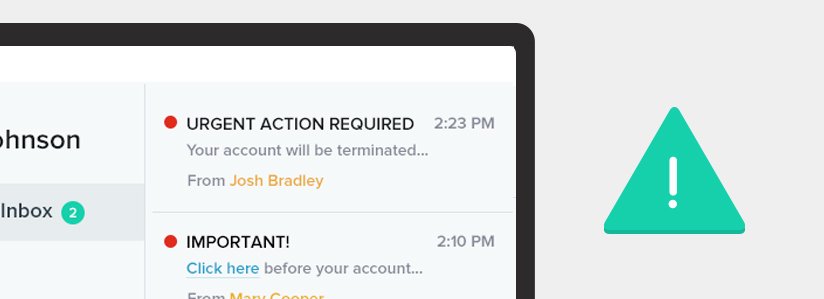
- Urgent Action Requested! — Phishers try to use the threat of immediacy as reason for users to respond. If the message you receive is insisting that you act upon it immediately, and it comes from a source that is sketchy, it’s best to hold off responding to it until it’s validity can be verified.
- Poor spelling and/or grammar — Whether it be spelling errors, incorrect grammar, or poorly phrased sentences, mistakes in the writing of a message are a dead give-away of attempted phishing messages. This doesn’t mean that every email with a typo is a threat to your security. However, if the message you receive is from an unknown source, and riddled with errors or funny sounding language, it’s best to avoid it all together.
- Something doesn’t look right about the message ‑ Whether it be the physical appearance of the message or the contents within, it is a safe bet to treat suspicious messages as threats until their authenticity can be confirmed.
- Mismatched URL(s) — Phishing attacks often attempt to disguise their intentions by using official or familiar sounding sources to trick users into clicking the malicious links.
- URLs contain misleading domain name — Similarly, the URL’s of a link found in an email can be altered to look as if it will take you to a legitimate site, instead pulling you right in to the phisher’s waiting hands. Simply put, avoid clicking on anything in these emails.
- Message asks for personal or login information — Occasionally, you might receive emails claiming to be from legitimate social media (Twitter, LinkedIn, etc.) or payment and banking sites (PayPal, Venmo, etc.), requesting your login for confirmation. This is a sure-fire sign that you are dealing with an attempt to access your personal information. Reputable businesses will never ask for this kind of information via email.
- Offer is too good to be true — Phishing messages often attempt to lure unsuspecting people in with some sort of offer, like a sale or limited-time promotion. In general, if the offer is too good to be true, it is, probably just that: untrue.
- You didn’t initiate the action — Sometimes, attacks are framed in messages purporting to be the response to some request the user has made. The message typically asks for some sort of response requiring a login as means for accessing your information.
- Emails claiming to be confirmation of complaints received/filed — Along those lines, some phishing attempts will disguise themselves as a response to the user filing a complaint. They will require you to login to something as confirmation of the action, and can gain access to personal details if the messages are not handled correctly.
- Message appears to be from the government — Even more common are messages claiming to be from governmental agencies, sometimes citing violations or complaints received against the user. Falsifying authority allows the attacker to gain your personal information through intimidation and fear of potentially devastating legal actions. These types of interactions are never handled via electronic messaging or telephone calls.
- Message says you’ve won a contest you haven’t entered — If you get a message congratulating you on winning a competition you don’t remember entering, it is highly likely that it is not simply your lucky day.
- Message asks to send money to cover expenses — This seems self-explanatory, but it can be rather deceptive. We’ve all heard of the mysterious prince who needs to off-load money and is willing to give it to you for free. Phishing techniques are always evolving, and more frequently contain personalized messages, which are designed to seem real enough for a user to believe them.
- Emails claim to be from person stranded in foreign country — Similarly, whether it’s a name you recognize or not, receiving an email from someone claiming to be stranded far away in desperate need of your help should raise some red flags. These are almost always attacks; delete them unless you can guarantee that they’re not.
- Emails claim to be from reputable news organizations – Some attacks will attempt to lure users in by sending links to what appear to be articles from reliable sources, ones that are sure to draw the eye in. They’ll ask you to click on links within the message which should take you to the piece you want to read; they are malicious entry-points which allow scammers to access sensitive information.
- Emails sound desperate or are threatening harm if action isn’t taken — It is a good bet that a message containing aggressive language regarding the urgency with which you respond is an attempt to scare you into unwillingly forking over private information. Unless you are already aware of a situation, receiving a message out-of-the-blue requiring your full and immediate attention should be regarded with skepticism.
Now that you know what to look for, it’s up to you to develop a way to prevent phishing attacks — either through implementation of companywide email management best practices or by educating your employees on the following safety tips:
Top 22 Email Management Tips to Prevent a Phishing Attack
- Never give out personal information — It’s simple: the best way to avoid falling for these scams is to simply never divulge personal information via emails or through links found in emails.
- Never share your password(s) — While it may seem innocuous, keeping your password to yourself significantly downplays the risk of others accessing personal accounts.
- If it seems suspicious, it likely is suspicious — Trust your gut feeling. If the message looks like it could be malicious, don’t take any action until it can be verified.
- Never visit your bank’s website using links in emails — As a matter of safety, don’t open links to any bank accounts or payment applications that come via email. Access the bank’s site via a secure web browser to guarantee that your information is safe.
- Be wary of pop-up menus — Some phishers will attempt to get users to enter their personal information on pop-up menus in an effort to disguise their attack. If an email requires this, it is likely a scam.
- Don’t believe everything you see — Whether it’s the name that is displayed or the layout of the message, it’s important to remain skeptical of messages which seem out of the ordinary. Hover over links within the message if you think they are suspicious; the link will display it’s intended destination, which can indicate its true nature.
- Analyze the greeting — Less sophisticated phishing attempts will contain generic terms like “Valued Customer” or “Dear Member.” Legitimate operations will typically use personal greetings in their official communications.
- Review the signature — A lack of details about the author of the message, or how to contact the company in question can be a strong indication that
- Double Check — Call individual or office which purportedly sent the email to confirm legitimacy. Name check the sender by calling or contacting them separately from the email chain. This can alert the company of a potential threats
- Beware of urgent/threatening language — Unless you personally know the sender of the email, disregard messages which threaten repercussions for unresponsiveness. Don’t fall for phrases like “urgent action required” or “your account will be terminated.” They are only meant to frighten you in to divulging your information.
- Don’t open anything — If you don’t know the sender or are unsure about the nature of the message AT ALL, don’t open any attachments to the message.
- Think before you click — Don’t click on links in messages that are dubious in nature. If there is a doubt in your mind about an email’s validity, it is safer to avoid opening or clicking anything.
- Be sure to report phishing/malicious/scam emails — The best way to eradicate the threat of phishing emails is to keep note of them when they happen to you, and report them to authorities, like IT or web administrators, if possible.
- Keep informed about phishing techniques — These scams are continually evolving, so it is important to be aware of the latest trends. Stay up to date by reading articles or forums, and take note when others around you describe attempted attacks.
- Expect the unexpected — As they evolve, phishers will try to find new and different ways to trick users. To stay ahead of the game, always be proactively thinking about where a message comes from and what it contains.
- Implement anti-phishing tools/anti-virus software/use firewalls — Most every email server has built-in tools to help identify and prevent phishing emails. There are plenty of additional resources available online if your server does not have this feature.
- Verify a site’s security — If there’s even a shred of doubt about the validity of the site or message, do the due diligence and spend five minutes verifying the security of the site. If it doesn’t have any credentials, or if they’re inexplicably hard to find, be very wary of proceeding. If you are tech-savvy enough, you can even check the DNS certificate of the website itself.
- Check your accounts regularly — One of the best ways to ensure that your accounts have not been compromised is to login to them on a regular basis. This applies to bank accounts as well as social media accounts.
- Keep your system up to date — As often as phishers are updating their techniques, it’s important to stay up to date on the ways to prevent their phishing emails from reaching mailboxes. Making sure you have the latest version of software is an easy way to stay one step ahead of attackers.
- Enhance the security of your computer — Use the wide array of available options to provide a security system for your accounts. There are plug-ins and extensions that can be downloaded and installed on web browsers that can recognize malicious sites instantaneously, which can help educate users on identifying and preventing attacks.
- Phishing knows all languages — As the ability to translate becomes more and more readily available, the amount of variations of possible phishing attacks grows. It takes very little effort to alter the language of most phishing attacks, so be aware that they may come from anywhere and in any number of different dialects.
- Inbound email sandboxing — Some web services offer the ability to send suspicious files to a cloud-hosted location to be analyzed for potential threats. This is a tool called Sandboxing, which can be helpful if you or your organization is unsure about a string of emails.
The threat of malicious phishing scams and their repercussions has been present since email began to gain popularity, and as the world’s culture has become more and more reliant on technology, the types of attacks used have grown almost exponentially. Methods for identifying phishing attacks that used to be fool-proof are now the jumping-off point for the attackers to develop new tricks.
To effectively identify and prevent phishing attacks, users should at least have base-level knowledge of what to look for and what techniques they can use to protect themselves from becoming a victim.
Detecting an attack can be difficult, because many users don’t really know how to recognize them. It requires users to develop an understanding of the various forms of attacks, and subsequently address digital communications with a degree of skepticism.
Intradyn is an information archiving company that specializes in providing email and social media archiving solutions to organizations all around the world. If you’re in need of an archiving solution to help you improve your email management, contact us today.

